Nowadays, the historical theme is slipping away from the media focus and unfortunately readers are becoming less and less attracted by any book or novel of such type. However, in an era where the commercialism rules, Galina Zlatareva managed somehow to write a novel telling us events which were of great significance about my birth country Bulgaria, which happened around the middle of the XIX century.
“The medallion” is a two part historical novel which follows chronologically the organization, the preparation, the outbreak and the decline of the Bulgarian revolution. The author not only does reveal historical motives in her novel, but also shows a brilliant sense of drama, presenting to the readers the life cycle of a simple Bulgarian merchant Gavril Hlutev, who evolves mentally to rise above the others and to turn into their spiritual leader and personal ideal, giving himself the name Georgi Benkovski.
At the same time there is a contemporary comparison with today’s world of mafia and corruption where the American citizen George Benkovski, who incidentally was named after the great ancient Bulgarian predecessor, ends up fighting for his life and the right for real justice to be resurrected in modern Bulgaria.
The story takes place in various countries however it is mainly focused on how the abrupt diplomatic changes in Europe, thoroughly dictated by the great strategist Otto von Bismarck, had such a great impact on all Balkan countries fate, one of which was situated at the heart of the Ottoman Empire and yet it strived for its freedom like the others, but gained it a few years after everyone else.
Personally I find both parts of the novel really intriguing because of my great interest in history as a whole. Many readers were amazed by the style of the author basically because she managed to mix three completely different story plots which eventually appeared to be the life stories of Bulgarian “heroes”. Once, a person dives into the spectrum of all the heroic and brave personalities of the main characters in the novel and compare them to the cowardly qualities of the ex and contemporary Bulgarian “leaders”, they realise how melancholy a reality could be.
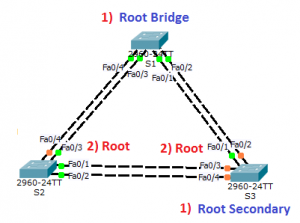
Scenario 2: Switches using two ports for interconnection
OK, folks, let’s make a quick resume on what I have already covered in my previous examples. I assume that everyone is familiar now that the Spanning-Tree Protocol does not function properly before the network has converged. Also, if you want to control it well, the best practice is first to sketch what you want as a result, then to try it in a lab or a simulator, and finally to implement it onto your network.
Now, that the basics are known, I move on to the other example where the interconnection between the switches is done by using two ports on each switching device. It is important to note that in my case I am managing the flow of five VLANs as follow:
- VLAN 40 – Management
- VLAN 20 – Staff
- VLAN 30 – Students
- VLAN 50 – Guest (WiFi)
- VLAN 100 – VoIP
Also keep into account all the STP Variants available out there. There are proprietary ones for the Cisco Layer 2 devices, too. Just for the record the main ones can be organized in the following table.
A quick off topic: as in the example given I am working with Cisco devices, my current explanation is directed to those one precisely. There is not a visible difference between PVST+ and Rapid-PVST+ technologies used. However, keep in mind that Rapid-PVST+ in many cases can be used to integrate Cisco switches with other company’s Layer 2 devices. What’s more, professionally speaking, it is best practice to keep your network up to date, so, please use Rapid-PVST+ as it comes with a bunch of new features, its default timers are: 2 seconds – hello timer, 15 seconds – forward delay timer, and 20 seconds – max-age timer (offers much greater convergence compared to PVST+) and also supports a fall back mechanism if there are older switches in your network infrastructure.
Now, recall the example with the timelines from scenario 1 explanation. It is the same case here, too. The thing is that with the following few configuration lines I try to achieve a different Spanning Tree Topology for each VLAN in the network each one having its own Root Bridge and port roles.
For VLAN 40 the following set of commands are issued to the three switches.
Port-priority value can vary from 16 to 240 in a 16 value interval. Cost value can vary from 1 to 200000000. For both commands the lower the number the higher the priority.
This gives this final outcome:
The same procedures are applied to all VLANs that exist in the network. This last table systematizes the final outcome wanted.:
Tip: If other outcome is desired, first scheme up what you want to do and then go ahead.
Not surprisingly, one of the fastest developing sectors is the IT one and every day we collide with an infinite amount of proofs for the inevitable fact that mankind would basically not exist with its internet cut down, for example. The starting point of this article is the very important reason to build up a redundancy network in a medium or a small enterprise, besides, the example provided on the following picture could be implemented on all types of architectures aiming to achieve this.
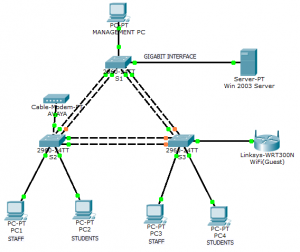
Moreover, Layer 2 redundancy in a network seriously depends on the interconnection between the Layer 2 devices, unfortunately, not every company can afford to buy three Cisco switches. What’s more, a small/ medium company neither really needs any core switches, for example. Therefore, the necessity for more switches is based on the number of users and services in a company, but the example provided can be applied to any network requiring different budgets, whose main goal is to cover the redundancy aspect in a company.
At first place, it is the cabling that has to be taken into account. The three switches are using two interfaces to interconnect to their neighbors. You can interconnect the switches as many times as you want, but be careful because you might need interfaces for later configuration and their number is not infinite! On the other hand, it’s not a bad practice if you interconnect the Layer 2 devices by using only one port for the interconnection. Watch out for the interface speed! It is preferable to have higher speeds for those interconnections (1Gbps/ 10Gbps), as they will be trunks; however, the implementation can vary depending on different situations. In order to avoid confusion, the word trunk here is used regarding the Cisco terminology (forget any HP terminology for now), which basically means a link that “carries” VLAN tagged traffic. If you are not quite familiar with this, I recommend you to read an article or two with more explanation on how a trunk link works. Also, pay attention to how many VLANs you want to implement in your network, but assuming this is a medium to small network there will be at least three VLANs (Management, Staff and Guest). Of course there might be more than those.
Scenario 1: Switches using only one port for interconnection
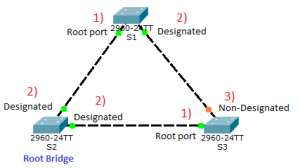
STP works properly only when the network has converged.
- This means that every switch has to go through an election process in which a Root Bridge is elected. The Root Bridge is the switch with the lowest BID (Bridge ID)
- Right after this the switches have to determine which roles their ports are going to take. Firstly, the Root ports are elected. In STP every switch determines one Root port for itself, except for the Root Bridge.
- Any port that is not a Root port is left with the choice of being Designated port or Non-Designated port. The election is based on a competition where the switches compare their path cost to the Root Bridge. If those values match, there is a comparison between the BIDs of the switches. The one that wins the competition has its port Designated and the one that loses – in Non-Designated. The Rood Bridge’s ports are automatically put as Designated ones.
As a network administrator you would probably like to have more control over the election process and you would be right. You would have different flows of data that must take different paths in your network, and you would definitely want to take this into your full control.
To do that, firstly, you need to know the number of the VLANs that your network implies. To make it more understandable, imagine that your network exists in many different timelines. In each one you need to take care of every VLAN in your network so you have to build up a different spanning-tree scheme for every case. Make sure you have schemed-up what you want to do before implementing it. To control the election process you can use the proper commands for the equipment that you use in your network. For Cisco switches to change the priority of a switch in order to control its role use this command:
Switch(config)# spanning-tree (Vlan #) priority (highest – 4096; lowest – 32768)
In Scenario 2, I will explain a more complex setup between switches using two ports for interconnection.
Titanic has always come to mind as an image of perfection. The project responsible for the construction of the biggest and the most robust steamer in the world received a lot of attention and admiration as an outstanding achievement. However, all superlatives have sunk with the ship during its first voyage on 14th of April, 1912. The unexpected, collision with an iceberg, actually could have been foreseen and escaped, yet it was highly possibly considered as less probable given the huge mass and the solid structure of the ship. Eventually, it turned out that all necessary resources to cope with such crisis had not been enough, which had considerably worsened the consequences of the surprising event.
If we take the Titanic example as a base, a project could experience various difficulties because of different reasons throughout its life cycle. Generally, each and every project has a Risk Analysis in order to cope with all difficulties, but by definition, this risk takes into account only predictable situations. According to Liz Lee-Kelley, the literature refers to unexpected situations as such of small probability but of a significant impact. The normative planning management relying on a Risk Analysis, suggests that it is possible to plan in advance every uncertainty. However, judging by experience, the knowledge that we have at the beginning of a project is never complete because we are not aware how exactly the project will pan out, and thus we can only make assumptions. In other words, it is possible that some unexpected situations happen.
There are solutions which address the before mentioned issues. They take advantage of internal and external sources of expertise by relying on intensive communications as well as on formal and informal practices. These practices enclose mainly negotiations with the client(s), with the stakeholders and the sponsor(s) of the project and generally aim to plan over and to reorganize the execution of the project by applying changes to its timetable, accumulating extra costs, etc.
The more a project is big and is complex, the bigger the chance to have cost overrun exists. And the bigger this chance is, the more probable that political maneuvers happen exists. Actually, no matter the project and its size, political games exist during all of the phases of its life cycle. They are an inevitable part of a project and it’s of high interest to anyone implicated in the project to be able to analyse the current situation and take rational actions based on his/hers analysis. More, regarding political games can be found in the next article.